My First Post
目录
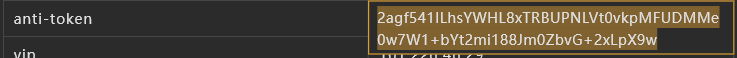
目标:anti_token
版本:7.85
方法:info3
2agf541ILhsYWHL8xTRBUPNLVt0vkpMFUDMMe0w7W1+bYt2mi188Jm0ZbvG+2xLpX9w
2ag开头的这串token值
随便拿一组数据
DeviceNative.info3 is called: context=android.app.ContextImpl@ffc87da, j14=1764768452533, str=zViMp2Gx
DeviceNative.info3 result=2agrkNsQuOsKezPdFVShcT2bJCorfdaaKJgTXu6jxdmlUZP3gzkACbO76NEWjP9PKzb
#include<Windows.h>
#include<stdio.h>
FARPROC MsgBoxAddr;
BYTE PatchCode[7] = { 0xe9,0 };
BYTE OldCode[7] = { 0 };
DWORD OldState;
void hook();
int WINAPI backdoor(HWND hWnd,
LPCSTR lpText,
LPCSTR lpCaption,
UINT uType);
void main();
void hook() {
// 获取user32.dll中的MessageBoxA函数地址
MsgBoxAddr = GetProcAddress(GetModuleHandle(L"user32.dll"), "MessageBoxA");
// 计算需要hook到的函数地址
DWORD targetAddr = DWORD(&backdoor) - DWORD(MsgBoxAddr) - 5;
memcpy(&(*(PatchCode + 1)), &targetAddr, 4);
printf("jmp to %x\n", *((ULONG*)(PatchCode + 1)));
// 读取原本的5字节数据
ReadProcessMemory(GetCurrentProcess(), MsgBoxAddr, OldCode, 5, nullptr);
for (int i = 0; i < 5; i++) {
printf("%x ", OldCode[i]);
if (i == 4) {
printf("\n");
}
}
// 申请写的权限,写入需要patch的字节数据
VirtualProtect(MsgBoxAddr, 6, PAGE_EXECUTE_READWRITE, &OldState);
WriteProcessMemory(GetCurrentProcess(), MsgBoxAddr, PatchCode, 5, nullptr);
// 恢复权限
VirtualProtect(MsgBoxAddr, 6, OldState, &OldState);
}
int WINAPI backdoor(
HWND hWnd,
LPCSTR lpText,
LPCSTR lpCaption,
UINT uType
) {
puts("Successful Hook!");
// 写入oldCode,暂时恢复MessageBoxA函数
for (int i = 0; i < 5; i++) {
printf("%x ", OldCode[i]);
if (i == 4) {
printf("\n");
}
}
WriteProcessMemory(GetCurrentProcess(), MsgBoxAddr, OldCode, 5, nullptr);
MessageBoxA(NULL, "Hook", "Successful", MB_OK);
// 恢复hook
WriteProcessMemory(GetCurrentProcess(), MsgBoxAddr, PatchCode, 5, nullptr);
return 0;
}
void main() {
hook(); // inline_hook
MessageBoxA(NULL, "woodwhale", "Title", S_OK);
}
模拟执行
补环境
搭好框架后先模拟执行 JNI_OnLoad
Read other posts